什么是打嗝扫描仪?
Burp Scanner is a tool for performing automated discovery of security vulnerabilities in web applications.打嗝扫描仪是用于执行在Web应用程序的安全漏洞的自动发现工具。 It is designed to be used by penetration testers, and to fit in closely with your existing techniques and methodologies for performing manual and semi-automated penetration tests of web applications.它被设计用来通过渗透测试,并紧密配合您的现有技术和进行手动和Web应用的半自动化渗透测试方法。
Using most web scanners is a detached exercise: you provide a start URL, click "go", and watch a progress bar update until the scan is finished and a report is produced.使用大多数Web扫描器是一种超然的练习:你提供一个开始的网址,点击“Go”,然后看进度条更新,直到完成扫描和报告的产生。 Using Burp Scanner is very different, and is much more tightly integrated with the actions you are already carrying out when attacking an application, giving you fine-grained control over each request that gets scanned, and direct feedback about the results.使用扫描仪打嗝是非常不同的,更紧密地与你的行动已经进行攻击时,一个应用程序,让您精细控制每个请求获得扫描,其结果直接反馈的综合。
Burp Scanner can perform two types of scans:打嗝扫描仪可以执行两种类型的扫描:
- Active scanning - The scanner sends various crafted requests to the application, derived from a base request, and analyses the resulting responses looking for vulnerable behaviour. 主动扫描 -扫描仪发出不同的制作要求的申请,请求来自一个基地,并分析了产生的反应行为寻找脆弱。
- Passive scanning - The scanner doesn't send any new requests of its own; it merely analyses the contents of existing requests and responses, and deduces vulnerabilities from those. 被动扫描 -扫描仪不发送它自己的任何新的要求,它只是分析和响应的内容,现有的请求,并推导出这些漏洞的。
You can initiate scans against your target application in two different ways:你可以对你的启动有两种方式的目标应用扫描:
- Manual scanning - You can send one or more requests from other Burp tools, to perform active or passive scans against those specific requests. 手动扫描 -您可以发送一个或多个工具的要求从其他打嗝,来对这些具体要求,主动或被动扫描。
- Live scanning as you browse - You can configure the Scanner to automatically perform active or passive scans against requests passing through the Proxy as you are browsing the application. 现场扫描你浏览 -你可以配置自动执行扫描仪通过代理传递活动请求反对或被动扫描你正在浏览的应用程序。
This approach to automated vulnerability detection brings a number of benefits to the penetration tester:这为自动化漏洞检测方法带来了对渗透测试的好处:
- Being able to perform quick and reliable scans for many common vulnerabilities on a per-request basis can hugely reduce your testing effort, enabling you to direct your human expertise towards vulnerabilities whose detection cannot be reliably automated.能够执行许多常见的漏洞扫描快速,可靠的基于每个请求的基础上可以极大地降低您的测试工作,使您能够直接对漏洞的检测你不能可靠的自动化人的专门知识。
- Results from each type of scan are displayed immediately, and can directly inform your other testing actions in relation to the individual requests involved.每个类型的扫描结果立即显示,并能直接通知有关您的其他测试行动所涉及的个别要求。
- Burp avoids a frustrating problem with other scanners, in which a monolithic automated scan takes an age to complete, with little assurance over whether the scan has worked, or whether it encountered problems that impacted on its effectiveness.打嗝避免了与其他扫描仪令人沮丧的问题,其中一个单片自动扫描时间来完成一个时代,几乎没有保证,对是否扫描了工作,还是遇到的问题,关于其有效性的影响。
By controlling exactly what gets scanned, and by monitoring in real time both the scan results and the wider effects on the application, Burp Scanner lets you combine the virtues of reliable automation with intuitive human intelligence, often with devastating results.正是得到通过控制扫描,并通过实时扫描结果和双方在更广泛的应用效果监测,打嗝扫描仪可以让你把人的智力与直观可靠的自动化的优点,结果往往造成毁灭性。
Active scanning主动扫描
In this mode of scanning, Burp takes an individual request to the application, called the "base request", and modifies it in various ways designed to trigger behaviour that indicates the presence of various vulnerabilities.在这种扫描方式,打嗝需要一个单独的应用程序的要求,被称为“基地的要求”,并修改了旨在触发行为,指出存在的各种漏洞的各种方式。 These modified requests are sent to the application, and the resulting responses are analysed.这些修改的请求被发送到应用程序,以及由此产生的反应进行了分析。 In many cases, further requests will be sent, based on the results of the initial probes.在许多情况下,进一步将发送请求的基础上,初步探测的结果。
This mode of operation generates large numbers of requests which are malicious in form and which may result in compromise of the application.这种运作模式会产生哪些是恶意的请求的形式和可能导致大量的应用妥协。 You should use this scanning mode with caution, only with the explicit permission of the application owner, and having warned them of the possible effects which automated scanning may have on the application and its data.您应谨慎使用这种扫描方式,只有在应用程序所有者的明确许可,并警告说,其中有自动扫描可能对应用程序及其数据可能对他们的影响。 If possible, scanning should be performed against non-production systems, and full backups performed prior to scanning.如果可能的话,应该执行扫描对非生产系统和完整备份之前完成扫描。
There are various well-known limitations on the types of vulnerabilities within web applications whose detection can be reliably automated.有各种众所周知的对Web应用程序的范围内可以可靠的自动检测漏洞的类型的限制。 Burp's active scanning capabilities were designed to focus on the kind of input-based bugs that scanners can reliably look for.打嗝的主动扫描功能的目的是着眼于对种输入的错误的扫描仪能够可靠地看看。 By avoiding the false positives that arise in other areas, Burp gives you confidence in its output, leaving you to focus on the aspects of the job that require human experience and intelligence to deliver.通过避免在其他领域出现的误报,打嗝让你在它的输出的信心,让你把重点放在与工作的若干方面需要人的经验和智慧来提供。
The issues that Burp's active scanning is able to identify mostly fall into two categories:打嗝的问题的主动扫描能够识别主要分为两类:
- Input-based vulnerabilities targeting the client side, such as cross-site scripting, HTTP header injection, and open redirection.基于投入的针对客户端漏洞,如跨站点脚本,HTTP头注射液,并打开重定向。
- Input-based vulnerabilities targeting the server side, such as SQL injection, OS command injection, and file path traversal.基于投入的针对服务器端的漏洞,如SQL注入,操作系统命令注入,和文件路径遍历。
Issues in category 1 can be detected with a very high degree of reliability.第一类问题可以检测的可靠性非常高的程度。 In most cases, everything that is relevant to finding the bug is visible on the client side.在大多数情况下,一切有找到相关的错误是在客户端可见。 For example, to detect reflected XSS, Burp Scanner submits some benign input in each entry point to the application, and looks for this being echoed in responses.例如,要检测反映的XSS,打嗝提交一些扫描仪在每个条目指向应用程序的良性投入,这是在响应呼应的样子。 If it is echoed, Burp then parses the response content to determine the context(s) in which the echoed input appears.如果是呼应,打嗝然后解析响应内容,确定上下文(s)在其中输入出现回荡。 It then supplies various modified inputs to determine whether strings that constitute an attack in those contexts are also echoed.然后,它提供各种修改意见,以确定是否构成一个字符串在这些情况下攻击也遥相呼应。 Burp Scanner has knowledge of the wide range of broken input filters, and associated bypasses, that arise with web applications, and it checks for all that apply to the context.打嗝扫描仪有破损的输入过滤器种类繁多,以及相关的绕过,这与Web应用程序产生的知识,并适用于所有的情况下检查。 By implementing a full decision tree of checks, driven by feedback from preceding checks, Burp effectively emulates the actions that a skilled and methodical human tester would perform.通过实施全面的检查决策树,从前面的反馈驱动检查,打嗝有效地模拟了行动,一支技术精湛,有条不紊人类测试将执行。 The only bugs that Burp should miss are those with some unusual feature requiring intelligence to understand, such as a custom scheme for encapsulating inputs.唯一的缺陷是打嗝应该错过与一些不寻常的情报,以了解需要,如用于封装输入自定义方案,特征的。
Issues in category 2 are inherently less amenable to automated detection, because in many cases the behaviours that are relevant to identifying the bugs occur only on the server, with little manifestation on the client side.第二类问题本质上是不适合进行自动检测,因为在相关的行为,以期找出错误只发生在服务器与客户端小的表现,许多案件。 For example, SQL injection bugs may return verbose database errors in responses, or they may be fully blind.例如,SQL注入漏洞可能会返回详细的数据库错误的反应,也可能完全失明。 Burp Scanner employs various techniques to identify blind server-side injection issues, by inducing time delays, changing Boolean conditions and performing fuzzy response diffing, etc. These techniques are inherently more error prone than the methods that are available in category 1.打嗝扫描仪采用各种技术来识别诱导时间延迟盲服务器端注入问题,布尔条件变化的响应和执行有用的比较模糊,等等,这些技术本身更错误的方法,这些方法比第1类可用的倾向。 Nevertheless, Burp Scanner achieves a high success rate in this area, reliably reporting numerous kind of issue that are difficult or laborious for a human tester to diagnose.然而,打嗝扫描仪实现了在这一领域的高成功率,可靠报告印发了许多种类的测试是为人类诊断困难或费力。
Passive scanning被动扫描
In this mode of scanning, Burp doesn't send any new requests to the application - it merely analyses the contents of existing requests and responses, and deduces vulnerabilities from those.在这种扫描方式,打嗝不会发送任何新的请求到应用程序 - 它只是分析了现有的请求和响应的内容,并推导出的这些弱点。 This mode of operation can be used safely and legally in any situation in which you are authorised to access the application.这种操作模式可用于安全,合法地在任何您有权访问的应用情况。
Burp Scanner is able to identify numerous kind of vulnerabilities using solely passive techniques, including:打嗝扫描器能够仅以被动识别技术,包括很多漏洞类型:
- Clear-text submission of passwords.明文提交密码。
- Insecure cookie attributes, like missing HttpOnly and secure flags.不安全的cookie的属性,如失踪的HttpOnly和安全标志。
- Liberal cookie scope.自由饼干范围。
- Cross-domain script includes and Referer leakage.跨域脚本包括和referer泄漏。
- Forms with autocomplete enabled.与自动完成的表格启用。
- Caching of SSL-protected content.缓存的SSL保护的内容。
- Directory listings.目录列表。
- Submitted passwords returned in later responses.提交密码后返回响应。
- Insecure transmission of session tokens.不安全的传输会话令牌。
- Leakage of information like internal IP addresses, email addresses, stack traces, etc.如内部IP地址,电子邮件地址,堆栈跟踪信息泄漏等
- Insecure ViewState configuration.不安全的ViewState的配置。
- Ambiguous, incomplete, incorrect or non-standard Content-type directives.暧昧,不完整,不正确或不标准的内容,类型的指令。
Many of these issues are relatively unexciting, and recording them is dull and repetitive for a human.其中许多问题都比较沉闷的,并记录他们单调,为人类重复。 But as penetration testers we are obliged to report them.但随着渗透测试我们有责任报告给我们。 Having Burp Scanner reliably mop up these issues as you browse an application is a time and sanity saver.经打嗝扫描器可靠扫荡了这些问题,你浏览一个应用程序是一个节省时间和理智。
Being able to carry out passive-only vulnerability scanning is beneficial in a range of situations:能够进行被动式漏洞扫描只在一个范围内的情况是有益的:
- Because passive scans don't send any new requests to the application, you can perform them safely against critical production applications where you want total control of every request that you send.由于被动扫描不会发送到应用程序的任何新的请求,您可以安全地执行它们对关键的生产应用中,你想要每个请求,您发送的完全控制。
- Some applications are aggressive in reacting to attacks, by terminating your session or locking your account every time an apparently malicious request is received.在一些应用程序是侵略性的攻击反应您的会议或通过终止您的帐户锁定每一个显然是恶意的请求接收时间。 In this situation, you may be restricted to piecemeal manual testing, but you can still use passive scanning to identify various kinds of issues without causing any problems.在这种情况下,您可能会受到限制零碎的手动测试,但你仍然可以使用被动的扫描,以确定不会造成任何问题的各种问题。
- If you don't (yet) have authorisation to attack a target, you can use passive scanning to identify vulnerabilities purely by browsing the application as a normal user.如果您不(还)有权限的攻击目标,你可以使用被动的扫描来识别浏览漏洞纯粹作为一个普通用户的应用。 For example, if you are proposing for a new penetration testing engagement, you can passively scan your target to get a feel for its security posture, and hopefully get some reportable issues in the bag before you even begin the official testing.例如,如果您正在寻找一个新的渗透测试参与建议,你可以被动地扫描你的目标得到了它的安全姿态的感觉,并希望得到一些收入囊中报告的问题之前,你甚至开始正式测试。
Initiating scans启动扫描
Manual scanning手动扫描
From anywhere within Burp Suite, you can select one or more HTTP requests, and send these to the Scanner to perform active or passive scanning.从套房内打嗝的任何地方,你可以选择一个或多个HTTP请求,并发送这些扫描仪进行主动或被动扫描。 For example, if you intercept an interesting request using Burp Proxy, you can initiate a scan against just this request using the context menu:例如,如果你拦截了一个有趣的请求使用打嗝代理,你可以启动扫描对眼前这个使用上下文菜单的要求:

Similarly, you can select sets of requests from within the Target site map or Proxy history, and send these in bulk to the Scanner.同样的,你可以选择从目标站点地图或代理的历史要求套,并发送批量这些扫描仪。 So, after browsing around an application and building up a comprehensive map of its content, you can tell Burp to scan specific areas of the application's functionality:因此,在应用程序和浏览周围建立一个其内容丰富详尽的地图,你可以告诉打嗝扫描应用程序的功能的特定领域:

If you select multiple items and send these for active scanning, Burp launches a brief wizard which lets you fine-tune your selection.如果您选择多个项目,并主动扫描发送这些,打嗝启动一个简短的向导,让您微调您的选择。 The first screen of the wizard offers you various intuitive filters to remove potentially unnecessary items (duplicates, already scanned items, media content, etc.), and shows you how many items will be affected by each filter:该向导的第一个屏幕提供各种直观的过滤器以消除潜在的不必要的物品(副本,已扫描的项目,媒体内容等),并显示出你有多少项目将被每个过滤器的影响:

The second screen of the wizard shows you a list of the remaining items, and lets you sort the table by various relevant properties, view the full requests and responses, and delete individual items:向导的第二个屏幕显示您的剩余项目清单,并允许您按不同的相关属性的表,视图全部请求和响应,并删除个别项目:

The wizard then completes and the selected items are sent for scanning in the usual way.然后完成该向导和选定的项目是在通常的方式扫描发送。
Live scanning现场扫描
A further way to initiate scans is to use the "live scanning" feature.另一种方法是使用扫描发起的“现场扫描”功能。 In this mode, you tell Burp what your target scope is for active and passive scanning, and it will automatically initiate active or passive scans against relevant requests as you use the application.在这种模式下,你告诉你的打嗝目标范围,是主动和被动扫描,它会自动启动对有关要求主动或被动的扫描,因为您使用的应用程序。 When operating in this mode, you simply need to browse around the application as a normal user, to show Burp where the application's content and functionality are, and it will work away in the background to find vulnerabilities for you.当在此模式下,你只需要浏览大约为普通用户的申请,如果申请打嗝显示的内容和功能,它会在后台帮您找到了漏洞。
When using live scanning, you have fine-grained control over the requests that Burp will automatically scan.使用实时扫描时,你有细粒度的请求,打嗝就会自动扫描控制。 If you have already configured a suite-wide target scope for your current work, then you can simply tell Burp to scan every request that falls within that scope.如果你已经配置了一套全方位的目标范围为你目前的工作,那么你可以简单地告诉打嗝扫描每一个要求,在这一范围之内。 Alternatively, you can define a custom scope to use for active and passive scanning.或者,你可以定义一个自定义的范围,使用主动和被动扫描。 In the example below, Burp has been configured to actively scan every request that is made to www.myapp.com, with the exception of login requests, and to passively scan every request that is made to any destination whatsoever:在下面的例子中,打嗝已被配置为每个被扫描积极向www.myapp.com,在登录请求例外,每一个被动扫描是向任何目的地的任何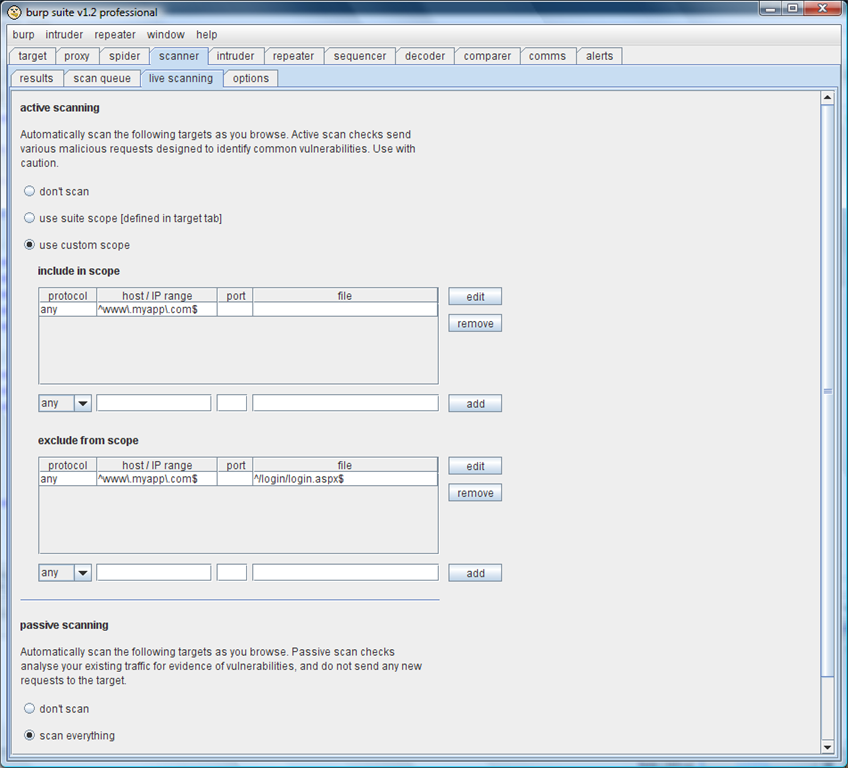 请求的请求:
请求的请求:
Note that the live scanning feature ignores requests for media resources (images, etc.) where the request does not contain any non-cookie parameters.请注意,现场扫描功能漠视媒体资源(图片等)如果请求不包含任何非cookie参数的要求。 Requests like these are virtually always for static resources which do not have any security significance, and so can be safely ignored by the scanner.像这些要求几乎总是静态的资源,没有任何安全意义,因此可以安全地通过扫描仪忽略。 (This does not apply to manual scanning - if you manually select items like these and send them for active scanning, then they will of course be scanned in the normal way.) (这并不适用于手动扫描 - 如果你手动选择这样的项目,并送他们主动扫描,那么他们当然会在正常的方式进行扫描。)
Active scan queue主动扫描队列
When you send requests for passive scanning, these are processed immediately.当你发送被动扫描,这些都是立即处理的请求。 Because active scans involve sending large numbers of requests to the server, requests sent for active scanning may be queued up.因为Active扫描需要发送大量的请求到服务器,请求派出主动扫描可能会排队。 A typical request with a dozen parameters will be scanned in a minute or two, and the scan queue is processed by a configurable thread pool, so the number of waiting items rarely grows very large.一个有十几个参数,典型的请求将被扫描在一两分钟,扫描队列处理的一个可配置的线程池,这样的等待项目数量很少的增长非常大。 As each item is scanned, the scan queue table indicates its progress - the number of requests made, the percentage complete, and the number of vulnerabilities identified.由于每个项目进行扫描,扫描队列表显示其进展 - 提出的请求数,完成百分比,以及确定的漏洞数量。 This last value is colourised according to the significance and confidence attached to the most serious issue:这最后一个值是根据colourised的意义和信心连接到最严重的问题:

You can double-click any item in the scan queue to display the issues identified so far, and view the base request and response for that item:你可以双击任何项目中显示的扫描队列目前已确定的问题,并查看相应的要求,该项目的响应: 
You can use the context menu on the scan queue to perform various actions:你可以使用上下文菜单扫描队列中执行各种操作:
- Show the details of the selected item.查看所选项目的详细信息。
- Cancel the selected item(s).取消选定的项目()。
- Scan the selected item(s) again.扫描选定的项目()了。
- Pause or resume the scanner.暂停或继续扫描仪。
Used in the ways described, Burp Scanner gives you fine-grained control over everything that it does, and integrates closely with your other testing activities.在使用方式描述,打嗝扫描仪为您提供细粒度的一切,它确实有效,而且与其它集成测试活动严格控制。 It lets you prioritise areas of an application that interest you, by browsing them using live scanning, or selecting them for scanning from the site map.它可以让你的应用程序的优先领域的兴趣,他们通过浏览使用实时扫描,或选择从网站地图扫描它们。 And it provides immediate feedback about those areas to inform your manual testing actions.并提供有关这些地区,告知你的手工测试行动即时反馈。
Reviewing results审查结果
In addition to the per-request view of discovered issues shown above, Burp Scanner maintains a central record of all the issues it has discovered, organised in a tree view of the target application's site map.除已发现的问题,每个请求的上述观点,打嗝扫描仪维护所有已发现它在目标应用程序的站点地图树视图组织的问题,中央记录。 Selecting a host or folder in the tree shows a listing of all the issues identified for that branch of the site:选择一个主机或在树中的所有文件夹显示为该网站的分支确定的问题清单:

Where multiple issues have been found of the same type, these are aggregated into a single item in the top-right panel.在多个问题得到相同类型的发现,这些聚合成一个在右上角面板的单一项目。 You can expand the aggregated item to view each individual instance of the issue.可以展开查看每个项目汇总的问题单独的实例。 Selecting an issue in the top-right panel shows the full detail for that issue in the bottom-right panel.选择在右上角面板显示了一个问题,在右下面板问题的全部细节。 This includes a customised vulnerability advisory, and the full requests and responses that are relevant to understanding and reproducing the issue.这包括一个定制的脆弱性的咨询,以及完整的请求和响应相关的理解和再现的问题。
The advisory includes a standard description of the issue and its remediation, and also a description of any specific features that apply to the issue and affect its remediation.该咨询包括对问题的描述和它的整治标准,也是适用的任何有关问题,并影响其整治的具体功能的说明。 In the example above, the cross-site scripting advisory tells us:在上面的例子,跨站点脚本咨询告诉我们:
- The request parameter in which the attack input is supplied (SearchTerm).请求参数,其中攻击输入提供的(搜索关键词)。
- The synactic context in which the input is returned in the response (within a piece of JavaScript, in a single-quote-delimited string).该synactic上下文中的输入是在响应中返回(在JavaScript会在一个引号分隔的字符串)。
- That the application escapes any single quote characters in our input, but fails to escape the backslash, allowing us to circumvent the filter.该应用程序,逃避我们的输入任何单引号,但未能逃脱反斜杠,使我们能够绕过过滤器。
- The exact proof-of-concept payload which Burp submitted to the application, and the form in which this payload was returned.确切的证明了概念有效载荷的打嗝提交申请,并在此有效载荷被退回的形式。
- That the original request used the POST method, and Burp was able to convert this to a GET request to facilitate demonstration and exploitation of the issue.原来的请求中使用POST方法,和打嗝能够转换为一个GET请求,以便示范和剥削的问题。
Every issue that Burp Scanner reports is given a rating both for severity (high, medium, low, informational) and for confidence (certain, firm, tentative).每一个打嗝扫描仪给出的评级报告,无论是严重的问题(高,中,低,信息)和信心(肯定的,坚定的,暂定)。 When an issue has been identified using a less reliable technique, Burp makes you aware of this, by dropping the confidence level.当一个问题已经确定使用一个不太可靠的技术,打嗝使你意识到这一点,通过删除的信心水平。
Alongside the advisory, Burp shows the requests and responses that were used to identify the issue, with relevant portions highlighted.除了咨询,打嗝显示了请求,被用来确定问题,与有关部分的突出反应。 You can review these to see how Burp identified the issue, and quickly understand the nature of the vulnerability.您可以查看这些,看看如何确定的打嗝问题,并迅速了解该漏洞的性质。 You can also send the request directly to other tools to manually verify the issue, or fine-tune the proof-of-concept attack that was generated by Burp:您也可以请求直接发送到其他工具来手动验证的问题,或微调证明型攻击的概念,是由打嗝产生:


Within the list of scan issues, you can modify the severity and confidence levels of individual or multiple issues (via the context menu), or delete issues altogether (via the context menu or using the 'del' key).列表扫描范围内的问题,您可以修改单个或多个问题的严重程度和置信度(通过上下文菜单),或完全删除的问题(通过上下文菜单或使用'德尔'键)。
Note that if you delete an issue, and Burp rediscovers the same issue (for example, if you rescan the same request), the issue will be reported again.请注意,如果您删除一个问题,打嗝重新发现同样的问题(例如,如果您重新扫描了同样的要求),这个问题将被报告了。 If instead you mark the issue as a false positive, then this will not happen.反之,如果你标记为假阳性,那么这将不会发生问题。 Therefore, deletion of issues is best used for cleaning up the Results tree to remove hosts or paths you are not interested in. For unwanted issues within the functionality you are still working on, you should use the false positive flag.因此,问题的缺失是最好的清理结果树删除主机或你不感兴趣的范围内的功能,你还在工作的不必要的问题英寸路径使用,您应该使用假阳性标志。
Scan optimisation扫描优化
Burp Scanner gives you detailed information in real time about all of the actions it is performing.打嗝扫描仪使您在有关的行动是执行所有实时的详细信息。 In the scan queue, you can monitor the progress of each individual base request that is being scanned.在扫描队列,您可以监控每个人的基础要求被扫描进度。 The table shows you the number of "insertion points" where Burp is placing payloads, and the number of attack requests that have been generated.下表显示了您的“插入点”,其中打嗝是把有效载荷,以及攻击的请求数已生成的数字。 (The latter is not a linear function of the former - observed application behaviour feeds back into subsequent attack requests, just as it would for a human tester.) (后者是前者不是一个线性函数 - 观察应用程序的行为反馈到随后的攻击请求,只是因为它为人类测试一样。)
This information lets you quickly see whether any of your scans are progressing too slowly, and understand the reasons why.这些信息可以让你很快地看到你是否有任何扫描进度过于缓慢,并了解原因。 Given this information, you can then take action to optimise your scans.鉴于此信息,您可以采取行动来优化您的扫描。 Within the scan queue, there is a context menu which lets you cancel or re-prioritise individual items.在扫描队列中,有一个上下文菜单,可以让你取消或重新个别项目的优先次序。 Within the Options tab, you can also optimise the scanner configuration based on what you have learnt about the application, using the options described below.在选项选项卡,您还可以优化扫描仪配置根据你对申请的经验教训,使用的选项说明如下。
Attack insertion points插入点攻击
A key factor in the speed and effectiveness of scans is the selection of attack insertion points.中的扫描速度和效益的关键因素是攻击插入点的选择。 Burp gives you fine-grained control over the locations within the base request where attack payloads will be placed, using the following configuration options:打嗝让您细粒度基地内的要求在有效载荷将放在攻击,使用以下配置选项位置控制:

The checkboxes let you define which locations within HTTP requests will have attacks placed into them:让你的复选框确定哪些地点将在HTTP请求到他们身上的攻击:
- The values of URL, body and cookie parameters.的URL,身体和cookie的参数值。
- Parameter name - if selected, Burp adds an additional parameter to the request and places attacks into the name of this parameter, often detecting unusual bugs that are missed if only parameter values are tested.参数名称 - 如果选中,打嗝增加了一个额外的参数的要求,并将其放在这个参数名的攻击,往往错过了检测,如果是唯一的参数值进行了测试不寻常的错误。
- HTTP headers - if selected, Burp places attacks into the User-Agent and Referer headers, often detecting issues like SQL injection or persistent XSS within logging functionality. HTTP头 - 如果选定,打嗝放置到用户代理和referer头攻击,往往在检测记录的功能,如SQL注入或持续性的XSS问题。
- AMF string parameters - For requests in Action Message Format, Burp places attacks into any string-based data types within the message. AMF的字符串参数 - 对于行动请求消息格式,打嗝放置到任何字符串为基础的数据类型在邮件的攻击。
- REST-style URL parameters - if selected, Burp places attacks into each directory or file name within the path portion of the URL. REST风格的URL参数 - 如果选定,打嗝放置到每个目录或文件名在URL路径的一部分的攻击。
You can also set a limit on the number of insertion points that Burp will attack within each base request.您还可以设置在插入点的数量打嗝会攻击在每个基地请求限制。 Occasionally, HTML forms may contain an excessive number of fields (hundreds, or more).有时,可能包含一个HTML表单的字段过多(几百人,或更多)。 If Burp performed a full vulnerability scan of every field, the scan would take an excessive amount of time to complete.如果打嗝执行完整的各个领域漏洞扫描,扫描将采取过多的时间来完成数量。 Setting a limit on insertion points prevents your scans from becoming stalled if they encounter forms with huge numbers of parameters.插入点上设置限制无法成为停滞不前,如果他们遇到大量的参数形式的扫描。 When this limit is applied, the item's entry in the scan queue will indicate the number of insertion points that were skipped, enabling you to manually review the base request and decide if it is worth performing a full vulnerability scan of all its possible entry points.当此限制被应用,该项目在扫描队列中的条目将显示插入点的数量被忽略,让您手动复查基地的要求,并决定是否值得执行完整的漏洞扫描其所有可能的进入点的。
You can tell Burp to use "intelligent attack selection".你可以告诉打嗝使用“智能攻击的选择。” This option causes Burp to perform or omit each type of server-side check based on the base value of each attack insertion point.此选项会导致打嗝履行或省略各种服务器端检查类型的基础上,每一个攻击插入点基值。 For example, if a parameter's value contains characters that don't normally appear in filenames, Burp will skip file path traversal checks for this parameter.例如,如果一个参数的值包含字符,通常不会出现在文件名,打嗝会跳过这个参数文件路径遍历检查。 Using this option can considerably speed up your scans, with minimal risk of missing actual vulnerabilities that exist.使用此选项可以大大加快你的扫描,与实际存在的漏洞缺少的风险很小。
The insertion point configuration lets you specify request parameters for which Burp should skip server-side injection checks.将插入点的配置,可以指定请求参数的打嗝应该跳过服务器端注入检查。 These checks are relatively time-consuming, because Burp sends multiple requests probing for various blind vulnerabilities on the server.这些检查都比较耗费时间,因为打嗝发送服务器上的各种漏洞盲目探测多个请求。 If you believe that certain parameters appearing within requests are not vulnerable (for example, built-in parameters used only by the platform or web server), you can tell Burp not to test these.如果您认为某些参数范围内出现的要求不容易受到攻击(例如,内置使用的平台或Web服务器仅参数),你可以告诉打嗝不试验这些。 (Note that client-side checks like cross-site scripting are always performed because testing each request parameter imposes minimal overhead on the duration of the scan if the parameter is non-vulnerable.) (请注意,如跨站点脚本的客户端检查总是执行,因为测试每个请求参数施加的扫描,如果参数是不容易的时间最少的开销。)
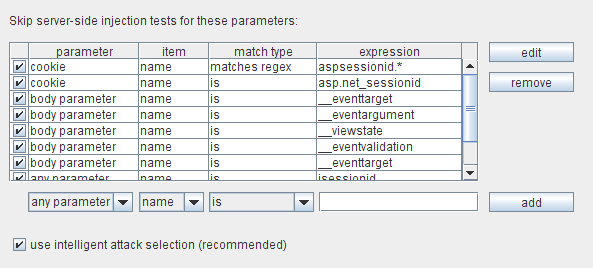
You can identify REST parameters by their position (slash-delimited) within the URL path, as well as by their value.你可以通过自己的立场(斜线分隔)在URL路径,以及其价值的REST参数。 To do this, select "REST parameter" from the parameter drop-down, "name" from the item drop-down, and specify the index number (1-based) of the position within the URL path which you wish to exclude from testing.要做到这一点,选择“休息参数”从参数落了下来,“名字”,从项目的下拉,并指定索引号的位置(基于1)在URL路径,您希望排除从测试。
You can also configure any parameters for which Burp should not perform any checks whatsoever.您还可以配置任何参数的打嗝不应该执行任何检查任何责任。
It is possible to specify fully customisable attack insertion points for active scanning, so you can specify arbitrary locations within a base request where attack strings should be placed.它可以主动扫描指定插入点完全可定制的攻击,所以你可以指定一个基本要求,在那里攻击字符串应该放在任意位置。 To use this function, send the relevant base request to Intruder, use the payload positions UI to define the start/end of each insertion point in the usual way, and select the Intruder menu option "actively scan defined insertion points".要使用此功能,发送相关基本要求入侵者,使用有效载荷位置的用户界面来定义开始/通常的方式中每个插入点结束,然后选择菜单选项入侵者“积极扫描定义插入点”。
Active scanning engine主动扫描引擎

These options let you fine-tune Burp's scan engine, depending on the performance impact on the application, and on your own processing power and bandwidth.这些选项可让您微调打嗝的扫描引擎,对应用性能的影响而定,并在您自己的处理能力和带宽。 If you find that your scans are running slowly, but the application is performing well and your own CPU utilisation is low, you can increase the number of scan threads to make your scans proceed faster.如果您发现您的扫描跑得很慢,但应用程序运行良好,你自己的CPU利用率很低,你可以增加扫描线进行扫描,使您更快的数量。 If you find that connection errors are occurring, that the application is slowing down, or that your own computer is locking up, you should reduce the thread count, and maybe increase the number of retries on network failure and the pause between retries.如果您发现连接错误发生,该申请正在放缓,或您自己的电脑上锁定了,你应该减少线程数,可能增加对网络故障和重试之间的停顿重试次数。 If the functionality of the application is such that actions performed on one base request interfere with the responses returned from other requests, you should consider reducing the thread count to 1, to ensure that only a single base request is scanned at a time.如果应用程序的功能是这样的行动在一个基地请求执行与其他要求,你应该考虑减少线程数为1产生的反应,干预,以确保只有一个基地的要求是一次扫描。
If you wish to avoid overloading the application, or to remain stealthy from a network perspective, you can use the throttle settings to add fixed or random intervals between requests.如果你希望避免超载的申请,或从网络的角度来看仍然隐身,你可以使用油门之间添加设置固定或随机的时间间隔要求。
Active scanning areas主动扫描领域

These options let you define which checks are performed during active scanning.这些选项让你定义的扫描检查,在积极进行。 Each check that is performed increases the number of requests made, and the overall time of each scan.每一个被执行的请求增加了多少检查,以及每个总时间扫描。 You can turn individual checks on or off, based on your knowledge of an application's technologies, or on how rigorous you require your scans to be.您可以打开或关闭个别检查,根据您的应用程序的技术知识,或如何严格要求你的扫描你的人。 For example, if you know that an application does not use any LDAP, you can turn off LDAP injection tests.例如,如果你知道一个应用程序不使用任何LDAP,你可以关闭的LDAP注入测试。 Or you can configure Burp to do a quick once-over of an application, checking only for XSS and SQL injection in URL and body parameters, before returning later to carry out more comprehensive testing of every vulnerability type in every insertion point.也可以配置打嗝做一个应用程序的快速一度超过,只检查中的XSS和SQL注入网址和身体参数,然后返回后要进行更多的每一次的插入点漏洞类型全面测试。
Passive scanning areas被动扫描领域

Passive scans do not send any requests of their own, and each passive check imposes a negligible processing load on your computer.被动扫描不会派遣自己的任何要求,并规定了每一个被动检查您的计算机上微不足道的处理负荷。 Nevertheless, you can disable individual areas of checks if you are simply not interested in them and don't want them appearing within scan results.然而,你可以停用个别地区的检查,如果你根本没有兴趣,他们不希望他们在扫描结果中。
Reporting报告
When you have finished testing, you can export a report of all or selected issues in HTML format.当你完成测试,可以导出所有的HTML格式的报告或选定的问题。 To do this, select the desired issues from the aggregated results display (you can multi-select individual hosts, folders, issues, etc.) and select "report issues" from the context menu.要做到这一点,请从汇总结果显示(可以多选单个主机,文件夹,问题等)所需的问题,并选择“报告问题”从上下文菜单。 The reporting wizard lets you choose various options for your report, including:报告向导,可以选择为您的报告各种方案,包括:
- The reporting format (screen- or printer-friendly).报告格式(屏幕或打印机友好)。
- The level of issue description and remediation to include.发行说明和整治水平,包括。
- Whether to show request and response details in full, or as extracts, or not at all.是否显示完整请求和响应的详细信息,或摘录,或根本没有。
- The categories of discovered issues to include or exclude.对发现的问题类别,包括或排除。
- Whether to organise issues by type, severity or URL.无论是组织的类型,严重程度或网址的问题。
- Report title, heading levels, etc.报告的标题,标题级别等
The report for the cross-site scripting vulnerability shown previously, with all detail turned on, and showing extracts of application responses in printer-friendly format, looks like this:对于跨站点脚本漏洞的报告表明以前,所有的细节打开,并显示在打印的格式的应用程序响应提取物,看起来像这样:

You can also report issues in XML format, to enable easy integration with other tools.您也可以在XML格式问题的报告,以使与其他工具轻松集成。 The XML has a flat structure, and contains a list of issues, with meta-information about issue type, URL, etc., reported within each issue element. XML具有一个平面结构,并包含一个问题清单与元左右问题的类型,URL等信息,报告在每个问题的元素。 The (internal) DTD looks like this: (内部)的DTD如下:
<!DOCTYPE issues [ <![DOCTYPE的问题
<!ELEMENT issues (issue*)> <!因素问题(问题*)>
<!ATTLIST issues burpVersion CDATA ""> <!ATTLIST问题burpVersion的CDATA“”>
<!ATTLIST issues exportTime CDATA ""> <!ATTLIST问题exportTime的CDATA“”>
<!ELEMENT issue (serialNumber, type, name, host, path, location, severity, confidence, issueBackground?, remediationBackground?, issueDetail?, remediationDetail?, requestresponse*)> <!元问题(序列号,类型,名称,主机,路径,地点,严重程度,有信心,issueBackground?,remediationBackground?,issueDetail?,remediationDetail?,requestresponse *)>
<!ELEMENT serialNumber (#PCDATA)> <!元序列号(#的PCDATA)>
<!ELEMENT type (#PCDATA)> <!元素类型(#的PCDATA)>
<!ELEMENT name (#PCDATA)> <!元素名称(#的PCDATA)>
<!ELEMENT host (#PCDATA)> <!元主机(#的PCDATA)>
<!ELEMENT path (#PCDATA)> <!元素路径(#的PCDATA)>
<!ELEMENT location (#PCDATA)> <!元素的位置(#的PCDATA)>
<!ELEMENT severity (#PCDATA)> <!元严重性(#的PCDATA)>
<!ELEMENT confidence (#PCDATA)> <!元信心(#的PCDATA)>
<!ELEMENT issueBackground (#PCDATA)> <!元issueBackground(#的PCDATA)>
<!ELEMENT remediationBackground (#PCDATA)> <!元remediationBackground(#的PCDATA)>
<!ELEMENT issueDetail (#PCDATA)> <!元issueDetail(#的PCDATA)>
<!ELEMENT remediationDetail (#PCDATA)> <!元remediationDetail(#的PCDATA)>
<!ELEMENT requestresponse (request?, response?)> <!元requestresponse(要求?,响应?)>
<!ELEMENT request (#PCDATA)> <!元素的请求(#的PCDATA)>
<!ELEMENT response (#PCDATA)> <!元反应(#的PCDATA)>
]> ]>
The serialNumber element contains a long integer that is unique to that individual issue.该序列号元素包含一个长整数,是独一无二的,个别的问题。 If you export issues several times from the same instance of Burp, you can use the serial number to identify incrementally new issues.如果您导出问题,从同一个实例打嗝好几次,你可以使用序列号来识别增量的新问题。
The type element contains an integer which uniquely identifies the type of finding (SQL injection, XSS, etc.).类型元素包含一个整数,唯一标识的发现(SQL注入,跨站脚本等)的类型。 This value is stable across different instances and builds of Burp.这个值是在不同情况下的稳定和打嗝生成。
The name element contains the corresponding descriptive name for the issue type. name元素包含了问题的类型对应的描述性名称。
The path element contains the URL for the issue (excluding query string).路径元素包含了这个问题(不包括查询字符串)的网址。
The location element includes both the URL and a description of the entry point for the attack, where relevant (a specific URL parameter, request header, etc.). location元素包括URL和一个入口点为攻击,说明在相关(一个特定的URL参数,请求头,等等)。
The other elements, some of which are optional and can be selected by the user within the reporting wizard, are hopefully self-explanatory.其他要素,其中一些是可选的,可以由用户选择在报告向导,是希望不言自明。